On 23rd April 2020 vpnMentor’s research team discovered a massive amount of incredibly sensitive financial data connected to India’s government-backed mobile payments app BHIM. According to the report, a massive 409 GB of files and over 7 million records had been uploaded and exposed. This breach was closed on 22nd May featur2020 by India’s Computer Emergency Response Team (CERT-In)
For those unaware, BHIM is a UPI enabled payments app that is backed by the central government of India through NPCI (National Payments Corporation of India). BHIM, like Google’s GPay, Flipkart’s PhonePe among others, is linked to all major banks across the country, to enable cross-bank transfer within minutes. It simply requires one’s UPI ID and a UPI Pin to transfer money to virtually any bank account.
“The website was being used in a campaign to sign large numbers of users and business merchants to the app from communities across India. All related data from this campaign was being stored on a misconfigured Amazon Web Services S3 bucket and was publicly accessible” the vpnMentor said.
The data was stored on an unsecured Amazon Web Services (AWS) S3 bucket, one of the most popular object storage services on cloud. The exposed S3 bucket was labeled “csc-bhim”, and vpnmentor’s team was quickly able to identify the developers behind the website “www.cscbhim.in” as the owners of the data. S3 buckets are generally public storage services when you purchase them, with developers being required to set security protocols on their own.
The data that has been exposed online includes Aadhar Cards, Caste certificates, Photos, PAN cards, Professional certificates. Other than this it also includes private personal user data such as Name, age, gender, address, caste, biometric details. According to the report it also contained documents and PII data of minors, with some records belonging to people under 18 years old.
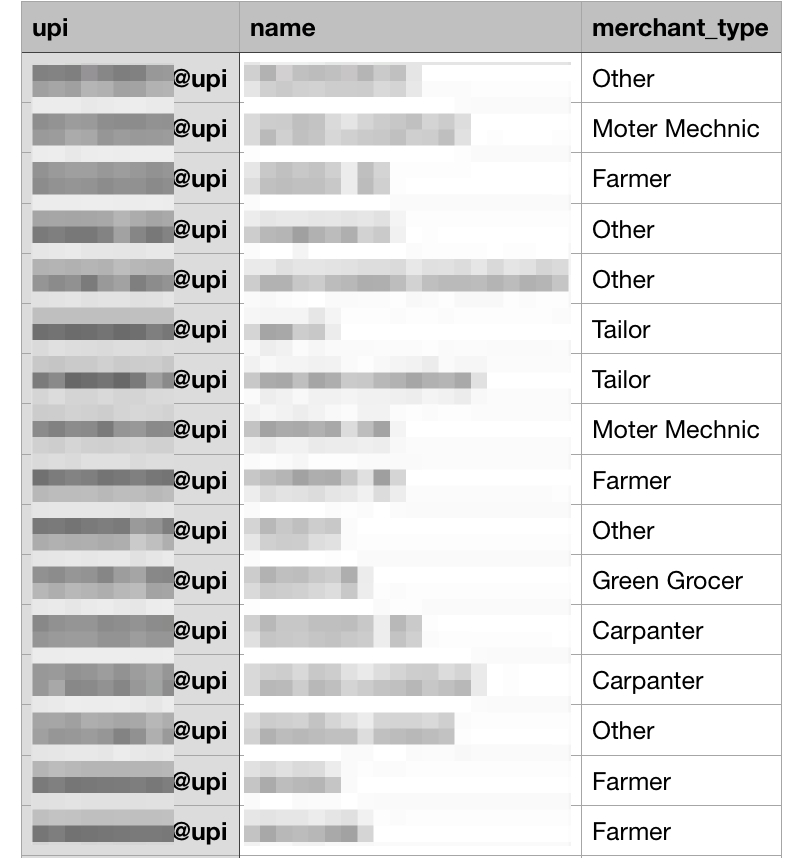
More importantly, several UPI IDs were publicly lying on the data in a CSV file. An image of that CSV data file was shared by vpnmentor’s team with The Tech Portal. Here’s a look:
The S3 bucket also contained an Android application package (APK), a file format used by Android’s operating system for the distribution and installation of apps. AWS Key pairs are the equivalent of admin user/password in Amazon’s infrastructure, potentially giving the holder of the key access to all data, the ability to start and stop servers, access the S3 bucket’s controls, and more.
No known exploits of the data have been spotted or reported for now. However, considering the sheer amount of data points that hackers got their hands on, along with the sheer user base of BHIM app, hackers would really require a small amount of those to institute a successful scam. We will constantly update the story as and when there is more on this.
The Tech Portal is published by Blue Box Media Private Limited. Our investors have no influence over our reporting. Read our full Ownership and Funding Disclosure →