Someone needs to hit the distress button right away! Yes, s**t just hit the fan! The already dire state of cybersecurity is expected to turn into an utter nightmare in the coming weeks(or months). You wanna know why? It’s because the source code for the IoT botnet responsible for some of the most recent and largest distributed denial of service (DDoS) attacks has been made public.
Brian Krebs, the popular cybersecurity reseacher, reported the unfortunate development and stated that it is the same botnet responsible for attack on his website(and OVH’s). The botnet is based on the trojan malware ‘Mirai’, and utilizes vulnerable or compromised Internet of Things(IoT) devices. It continuously scans for smart home systems protected by factory default or hard-coded login credentials and seeds them to report to a centralized ‘control’ server.
The botnet is, thus, powered by a slew of insecure routers, IP cameras, digital video recorders and other easily hackable devices and has led to fears that it can now practically be used by anyone to flood the internet with a DDoS attack. Sources have reported to Krebs that Mirai is one of the two malware families(the other being Bashlight) being employed to quickly create IoT-based DDoS armies. Botnets based on Bashlight are currently exploiting data from about a million IoT devices to flood the attack site with gigs of traffic.
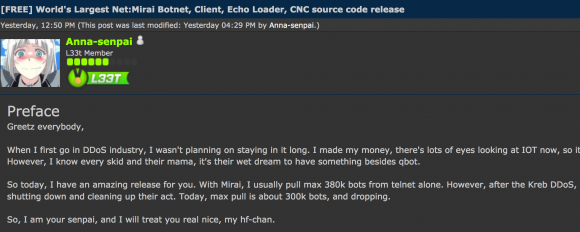
The source code has been released on the hacking community ‘Hackforums’ by a user/hacker with the nickname ‘Anna-senpai’. The hacker told the members on the platform that the source code was being released to the public in response to the increased scrutiny by cybersecurity researchers. In his post on the forums, he says that,
When I first go in DDoS industry, I wasn’t planning on staying in it long. I made my money, there’s lots of eyes looking at IOT now, so it’s time to GTFO.
So today, I have an amazing release for you. With Mirai, I usually pull max 380k bots from telnet alone. However, after the Kreb DDoS, ISPs been slowly shutting down and cleaning up their act. Today, max pull is about 300k bots, and dropping.
With the release of such a powerful malware, the hackers(on anybody who is in it for the fun) can now access the publically available code and add it to their arsenal. And since the code is available to all, it will become extremely difficult for the govt. authorities to put a halt to the chaos that’s upon them. It will become a little difficult for them to pin-point and track the ‘master’ operator of the malware. In addition, Krebs in the blogpost adds that,
My guess is that (if it’s not already happening) there will soon be many Internet users complaining to their ISPs about slow Internet speeds as a result of hacked IoT devices on their network hogging all the bandwidth.
On the bright side, if that happens it may help to lessen the number of vulnerable systems.
On the not-so-cheerful side, there are plenty of new, default-insecure IoT devices being plugged into the Internet each day.
It is like two faces of the same coin, that is morphing with each passing day. He’s also stated that infected systems can be cleaned up by simply rebooting them as it wipes the malicious data from the memory. But to protect your IoT device from repeated scanning and intrusion, you’ll need to change your default login credentials.
If you’re unaware, KrebsonSecurity website was recently hit with one of the largest DDoS attacks and kncked offline. With traffic amounting to a total of 620 Gbps, the attackers flooded his website in retaliation of him uncovering the masterminds behind some of the largest DDoS attacks in the last decade. His DDoS protection provider Akamai — who provides pro-bono services — to the website pulled support amid the attack and Krebs had to seek support from the Google Shield Project to bring back his website from the dead.
And after this, OVH, a french hosting company was attacked with the world’s largest-known DDoS attack. It was a record-breaking attack, where two simultaneous attacks hit the server and one of the two attacks alone peaked to 799 Gbps of traffic. The hackers had targeted Minecraft servers hosted on the OVH network, and the attack was carried out using a botnet madeup of over 145,000 IoT devices.
The Tech Portal is published by Blue Box Media Private Limited. Our investors have no influence over our reporting. Read our full Ownership and Funding Disclosure →






