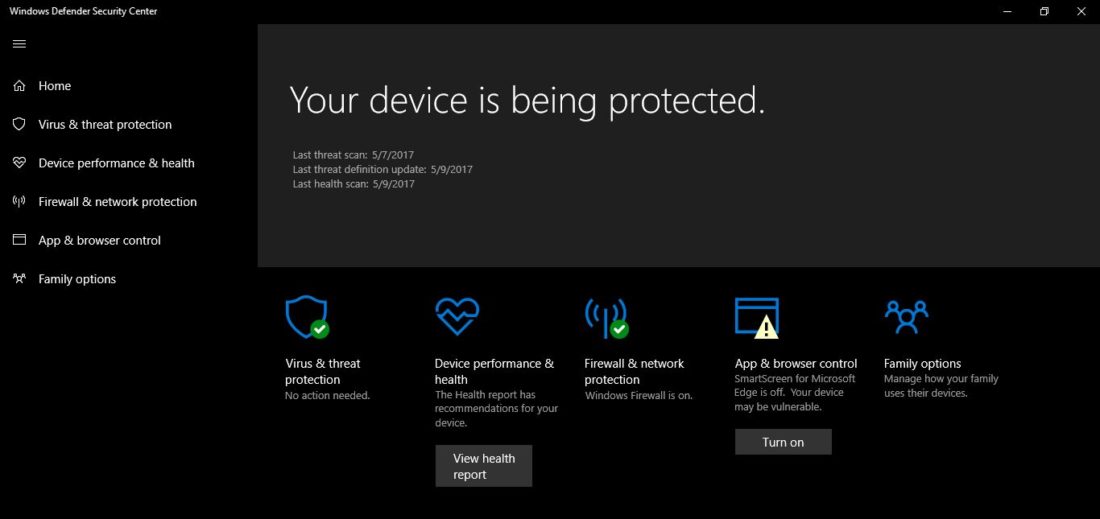
Microsoft has been particularly quick to squash a critical vulnerability in Windows Defender, which was reported a couple days back by Google Project Zero researchers Tavis Ormandy and Natalie Silvanovich.
The vulnerability was brought to the notice of the Redmond giant via Twitter, where Ormandy stated that it was the worst Windows remote code exec in recent memory. He stated that the problem was in Windows Defender, where the exploit worked even against default installations and was wormable – which means it could replicate itself on an infected PC and then automatically affect others as well – via email.
.@natashenka Attack works against a default install, don’t need to be on the same LAN, and it’s wormable. ?
— Tavis Ormandy (@taviso) May 6, 2017
In the official Chromium blog post, Ormandy details Windows Defender’s vulnerability and writes that the exploit can be spread via email. And the malware will spread across your system and to others on your network (or contact list) without you even interacting with the email even once. This is because one of the well-known components, i.e the anti-malware detection engines of the security software could be tricked into executing code
This is because one of the well-known components, i.e the anti-malware detection engines of the security software could be tricked into executing code included in a malicious email (or a webpage/instant message). This service scans website, links, files, and emails to keep intruders at bay but the embedded code will get executed while scanning, thus spreading this nasty malware. The importance of this component has been described as under:
The core component of MsMpEng responsible for scanning and analysis is called mpengine. Mpengine is a vast and complex attack surface, comprising of handlers for dozens of esoteric archive formats, executable packers and cryptors, full system emulators and interpreters for various architectures and languages, and so on. All of this code is accessible to remote attackers.
But, we no longer need to worry about this vulnerability being exploited because Microsoft has patched Windows Defender. Today, it has released an updated version of the security software, which your system should automatically pick in the coming day or two. This update is now available for the consumer, as well as IT versions of Windows 7, 8.1, RT and 10. You can force this update right away if you’re too concerned about your privacy and security. Just remember, the new version number of the engine should be 1.1.13704.0 or higher.
Talking about this super crucial vulnerability, the blog post mentions,
The update addresses a vulnerability that could allow remote code execution if the Microsoft Malware Protection Engine scans a specially crafted file. An attacker who successfully exploited this vulnerability could execute arbitrary code in the security context of the LocalSystem account and take control of the system.
Just released malware protection engine update to
address RCE vuln – Defender will autoupdate. https://t.co/rzn5QWo6sV— Security Response (@msftsecresponse) May 9, 2017
Microsoft was on the case the moment Tavis Ormandy made them aware of this critical vulnerability in their security software. The security developer teams at Redmond were able to work out a fix for the vulnerability in just a couple days.Microsoft’s handy work towards the elimination of the bug bagged Ormandy’s instant commendation.
Still blown away at how quickly @msftsecurity responded to protect users, can’t give enough kudos. Amazing.
— Tavis Ormandy (@taviso) May 9, 2017
The Tech Portal is published by Blue Box Media Private Limited. Our investors have no influence over our reporting. Read our full Ownership and Funding Disclosure →